9718856466,9990657855
eiidelhi@gmail.com
9718856466,9990657855
eiidelhi@gmail.com

GATE 2026 Important Questions in Computer Science & Engineering – CSE Welcome to EII - Your Gateway to Success!
Prepare for GATE 2026 with confidence using a handpicked set of important questions in Computer Science & Engineering (CSE), crafted by the expert faculty of Engineers Institute of India (EII). Renowned for its focused and high-quality coaching in CSE, EII is committed to helping you achieve excellence in the upcoming GATE exam.
Q.1 Which word completes the analogy "Fish is to Shoal as Lion is to _______"?
Answer: (A)
Explanation:
Analogies are based on relationships between pairs of words, so we need to determine the specific relationship and apply it consistently.
Step 1: Analyze the Relationship
Step 2: Apply the Relationship to Lion
Q.2 Which sentence is grammatically correct?
Answer: (A)
Explanation:
A - "It is I who am responsible" translates to "I am the one who am responsible," which is grammatically consistent:
Other options fail:
Q.3 Cars P and Q start from point X in Gurugram at 10 AM. Car P heads North at 25 km/h and travels continuously, while Car Q heads East at 30 km/h but stops after 1 hour. If both are equidistant from X at 11:30 AM, how many minutes did Car Q stop for?
Answer: (C)
Explanation:
Step 1: Distance by car P at 11:30 AM
Step 2: Distance by car Q
Step 3: Calculate Q’s travel time
Step 4: Find stoppage time
Q.4 Which statement is NOT true for all real 𝑥 regarding floor and ceiling functions?
Answer: (D)
Explanation:
The ceiling function ⌈x⌉ is the smallest integer ≥ x, and the floor function ⌊x⌋ is the largest integer ≤ x. We need to identify a statement that’s NOT true for all real x.
Common statement to test: ⌊x⌋ + 1 = ⌈x⌉
For x = 2.3:
For x = 2:
The statement ⌊x⌋ + 1 = ⌈x⌉ is NOT correct for all x.
Q.5 P and Q play chess. P wins 80%, draws 15%, and loses 5%. If they play 3 more matches, what is the probability that P wins exactly 2?
Answer: (A)
Explanation:
To find the probability that P wins exactly 2 of 3 chess matches against Q, given P's win rate is 80%, draw rate is 15%, and loss rate is 5%, we use the binomial probability formula. The outcomes are win, draw, or loss, but the question asks for the probability of exactly 2 wins, so we focus on wins versus non-wins.
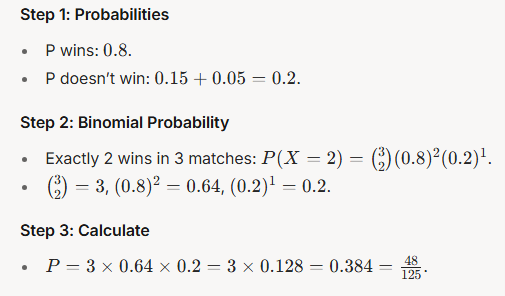
Q.6 Select the most logical sentence sequence to form a paragraph.
P. At once, without thinking much, people rushed towards the city in hordes with the sole aim of grabbing as much gold as they could.
Q. However, little did they realize about the impending hardships they would have to face on their way to the city: miles of mud, unfriendly forests, hungry beasts and inimical local lords – all of which would reduce their chances of getting gold to almost zero.
R. All of them thought that easily they could lay their hands on gold and become wealthy overnight.
S. About a hundred years ago, the news that gold had been discovered in Kolar spread like wildfire and the whole State was in raptures.
Answer: (D)
Explanation:
Step 1: Analyze Sentence Connections
Sequence and Flow
Q.7 If HIDE → 19-23-7-11 and CAGE → 5-2-17-11, what is the code for HIGH?
Answer: (D)
Explanation:
HIDE → 19-23-7-11
CAGE → 5-2-17-11
HIGH ⇒ 19-23-17-19
Q.8 A figure is reflected horizontally and then rotated 90° clockwise. Which is the resulting figure?
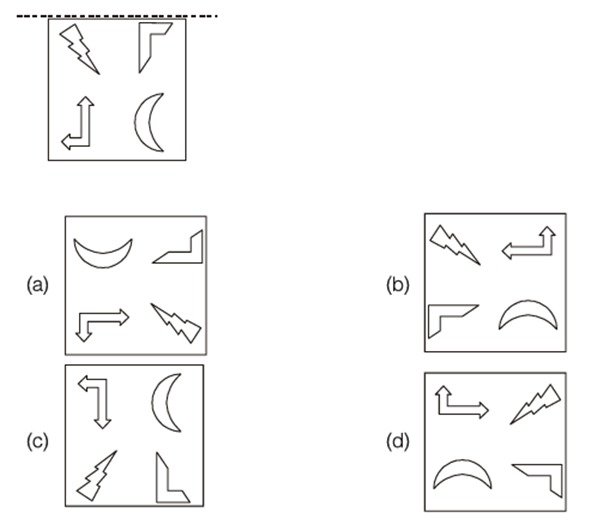
Answer: (Depends on actual figures shown)
Explanation:

Anti-clockwise figure

Reflection along horizontal line figure
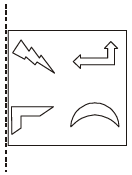
Q.9 Arrange in increasing order of lines of symmetry: Isosceles triangle, Equilateral triangle, Square, Circle.
Answer: (B)
Explanation:
The Correct Sequence of Objects Based on Increasing Number of Mirror Lines (Lines of Symmetry)
Q.10 A student has 0.8 and 0.6 probability of job offers from Company S and T respectively. What is the probability of getting both?
Answer: (B)
Explanation: P (S) = 0.8 P (T) = 0.6 P (S∩T) = P (S) . P (T) = (0.8) . (0.6) = 0.48
1. Which of the following Boolean expressions is equivalent to A⋅B + A‾⋅C?
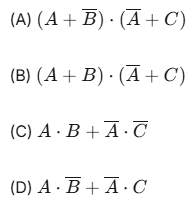
Using the consensus theorem or K-map, the expression A⋅B+A‾⋅C can be
simplified. Alternatively, we can verify by constructing truth tables or algebraic manipulation. The expression (A+B)⋅(¯A+C)
distributes to A⋅¯A+A⋅C+B⋅¯A+B⋅C
Since A⋅¯A=0, it simplifies A⋅C+B⋅¯A+B⋅C to Further simplification using K-map confirms it matches "A.B"+¯A⋅C.
2. A 4:1 multiplexer has how many select lines?
3. The output of a 2-input XOR gate is 1 when the inputs are:

4. The minimal sum-of-products form of the Boolean function F(A,B,C)=Σm(0,2,4,6) is:


5. In IEEE 754 single-precision floating-point format, the number of bits used for the exponent is:
6. A full adder has how many outputs?
7. The binary equivalent of -13 in 6-bit 2’s complement form is:
Explanation: Convert 13 to binary: 13=1101 13 = 1101 13=1101. For 6-bit 2’s complement of -13:

8. 
9. 

10. 

11. In the Karnaugh Map (K-Map), adjacency refers to:
12. A multiplexer with n select lines can select from how many input lines?
13. Which flip-flop is suitable for frequency division?
14. Which of the following binary operations is associative?
15. In floating point representation, the mantissa is:
16. Two's complement representation helps in:
17. What is the minimum number of flip-flops needed to design a MOD-6 counter?
18. The range of an 8-bit signed 2’s complement number is:
19. [MSQ] Which of the following circuits can be built using a multiplexer?
20. [MSQ] Which of the following are true about D flip-flop?
1. Which of the following addressing modes uses a constant value specified within the instruction?
2. The primary role of the control unit in a processor is to:
3. In a pipeline processor, a structural hazard occurs when:
4. Which of the following is a characteristic of RISC architecture?
5. The number of bits required to address 1MB of memory with word size of 1 byte is:
6. In instruction pipelining, which of the following hazards can be resolved using operand forwarding?
7. Which memory is the fastest in the memory hierarchy?
8. In DMA (Direct Memory Access), data is transferred:
9. The purpose of a pipeline in a processor is to:
10. In a 5-stage pipeline, the number of clock cycles required to complete n instructions (ideal case) is:
11. Which of the following is NOT a type of pipeline hazard?
12. Memory-mapped I/O uses:
13. What is the function of a control signal in a micro-programmed control unit?
14. Which of the following best describes locality of reference?
15. A cache with block size of 4 words and total 64 blocks can store:
16. Which technique is used to reduce the miss penalty in cache memory?
17. What is the key difference between interrupt and polling?
18. A hard disk is an example of:
19. [MSQ] Which of the following are pipeline hazards in a processor?
20. [MSQ] Which of the following are benefits of using cache memory?
1. What is the output of the following C code?
int main() {
int a = 5;
printf("%d", a++ + ++a);
}
(A) 11
(B) 12
(C) 10
(D) Undefined behavior
Answer: (D)
Explanation: Modifying and accessing a more than once without a sequence point leads to undefined behavior.
2. What is the worst-case time complexity of searching in a Binary Search Tree?
(A) O(log n)
(B) O(n)
(C) O(n log n)
(D) O(1)
Answer: (B)
Explanation: In worst case, the tree may become skewed like a linked list.
3. What is the maximum number of nodes in a binary tree of height h?
(A) 2h
(B) 2h+1
(C) 2h+1 - 1
(D) 2h - 1
Answer: (C)
Explanation: Maximum nodes in binary tree = 2h+1 - 1
4. Which of the following is not a characteristic of a stack?
(A) LIFO
(B) Can be implemented using arrays
(C) FIFO
(D) Push and Pop operations
Answer: (C)
Explanation: FIFO is a queue property. Stack is LIFO.
5. In a min-heap, the smallest element is always located at:
(A) The root
(B) A leaf node
(C) The middle
(D) Rightmost node
Answer: (A)
Explanation: In min-heap, the root is always the smallest element.
6. Which data structure is used for BFS in a graph?
(A) Stack
(B) Queue
(C) Priority Queue
(D) Hash Table
Answer: (B)
Explanation: BFS uses a queue to explore nodes level-wise.
7. Which traversal of a binary search tree gives sorted order?
(A) Pre-order
(B) Post-order
(C) In-order
(D) Level-order
Answer: (C)
Explanation: In-order traversal of BST gives values in ascending order.
8. Which of the following is a valid base case for recursion?
(A) if(n == 1) return 1;
(B) return n * fact(n - 1);
(C) printf("Done");
(D) while(n > 0)
Answer: (A)
Explanation: Base case is the condition to terminate recursion.
9. In C, which operator is used to access value at a pointer address?
(A) &
(B) *
(C) ->
(D) %
Answer: (B)
Explanation: * is the dereference operator.
10. What is the output of the following?
char *str = "GATE";
printf("%c", *(str+2));
(A) G
(B) A
(C) T
(D) E
Answer: (C)
Explanation: Index 2 of "GATE" is 'T'.
11. Which data structure is best suited for implementing undo operations?
(A) Queue
(B) Stack
(C) Heap
(D) Graph
Answer: (B)
Explanation: Stack follows LIFO, which fits undo operations.
12. In a singly linked list, deletion of a node at the end requires:
(A) O(1) time
(B) O(n) time
(C) O(log n) time
(D) O(n²) time
Answer: (B)
Explanation: You need to traverse the list to the second last node.
13. Which of the following statements is true?
(A) Every binary tree is a binary search tree
(B) Every binary search tree is a binary tree
(C) All heaps are binary search trees
(D) A heap is a type of linked list
Answer: (B)
Explanation: BST is a type of binary tree with ordering property.
14. Which function is used to allocate memory dynamically in C?
(A) malloc
(B) alloc
(C) init
(D) create
Answer: (A)
Explanation: malloc() is used for dynamic memory allocation.
15. In an adjacency list representation of a graph with V vertices and E edges, total space required is:
(A) O(V + E)
(B) O(V²)
(C) O(E)
(D) O(V)
Answer: (A)
Explanation: Each vertex stores list of adjacent vertices → O(V + E)
16. What is the time complexity of inserting an element into a binary heap?
(A) O(n)
(B) O(log n)
(C) O(1)
(D) O(n log n)
Answer: (B)
Explanation: Insertion requires upheap or "bubble up" → O(log n)
17. In which case will a queue become full?
(A) front == rear
(B) rear == size - 1
(C) front == -1
(D) rear == front + 1
Answer: (B)
Explanation: In array-based queue, if rear reaches end, it's full.
18. Which sorting algorithm is best suited for nearly sorted data?
(A) Selection Sort
(B) Insertion Sort
(C) Bubble Sort
(D) Merge Sort
Answer: (B)
Explanation: Insertion sort performs well on nearly sorted input with O(n) time.
19. (MSQ) Which of the following are recursive data structures?
(A) Linked List
(B) Stack
(C) Tree
(D) Graph
Answers: (A), (C), (D)
Explanation: Linked lists, trees, and graphs are recursive in structure. Stack is not recursively defined.
20. (MSQ) Which operations are allowed in an array-based queue implementation?
(A) Enqueue at front
(B) Dequeue from rear
(C) Enqueue at rear
(D) Dequeue from front
Answers: (C), (D)
Explanation: In standard queue: enqueue at rear, dequeue from front.
1. What is the time complexity of binary search in the worst case?
(A) O(1)
(B) O(n)
(C) O(log n)
(D) O(n log n)
Answer: (C)
Explanation: Binary search halves the search space in each step → O(log n)
2. Which sorting algorithm has the best average-case time complexity?
(A) Bubble Sort
(B) Merge Sort
(C) Insertion Sort
(D) Selection Sort
Answer: (B)
Explanation: Merge Sort has average-case time complexity of O(n log n)
3. In a hash table, what is the purpose of a collision resolution strategy?
(A) To sort elements
(B) To manage identical keys
(C) To handle two keys with the same hash index
(D) To remove duplicate keys
Answer: (C)
Explanation: Collision occurs when two keys map to the same index.
4. Which of the following is an asymptotic upper bound?
(A) Θ
(B) O
(C) Ω
(D) None
Answer: (B)
Explanation: Big-O provides the worst-case upper bound.
5. Which technique is used by Merge Sort?
(A) Greedy
(B) Dynamic Programming
(C) Backtracking
(D) Divide and Conquer
Answer: (D)
Explanation: Merge Sort splits the array, solves recursively, and merges.
6. What is the time complexity of Dijkstra’s algorithm using a binary heap?
(A) O(V²)
(B) O(V log V + E)
(C) O(V + E)
(D) O(E log V)
Answer: (B)
Explanation: Dijkstra with binary heap and adjacency list → O((V + E) log V)
7. In BFS, what data structure is used?
(A) Stack
(B) Queue
(C) Priority Queue
(D) Heap
Answer: (B)
Explanation: BFS uses queue for level-wise traversal.
8. Which one is not a greedy algorithm?
(A) Prim’s Algorithm
(B) Kruskal’s Algorithm
(C) Huffman Coding
(D) Bellman-Ford Algorithm
Answer: (D)
Explanation: Bellman-Ford is based on dynamic programming.
9. Which of the following is true about Dynamic Programming?
(A) Works only for problems with overlapping subproblems
(B) Requires sorting of input
(C) Used only for shortest path problems
(D) Uses divide-and-conquer
Answer: (A)
Explanation: Dynamic programming solves problems with optimal substructure and overlapping subproblems.
10. The best case time complexity for Quick Sort is:
(A) O(n²)
(B) O(n)
(C) O(n log n)
(D) O(log n)
Answer: (C)
Explanation: Best case occurs when the partition divides array evenly.
11. Which of the following algorithms always gives the optimal solution?
(A) Greedy
(B) Brute Force
(C) Divide and Conquer
(D) Dynamic Programming
Answer: (D)
Explanation: DP ensures optimal solution if problem satisfies optimal substructure.
12. What is the time complexity of traversing a graph with DFS?
(A) O(V²)
(B) O(V + E)
(C) O(V log V)
(D) O(E log V)
Answer: (B)
Explanation: DFS visits all vertices and edges once → O(V + E)
13. In which case will linear search be faster than binary search?
(A) Sorted arrays
(B) Unsorted arrays
(C) Linked lists
(D) Both B and C
Answer: (D)
Explanation: Binary search requires sorted data. Linear search works on both.
14. What is the worst-case time complexity of Quick Sort?
(A) O(n²)
(B) O(n log n)
(C) O(log n)
(D) O(n)
Answer: (A)
Explanation: Worst-case occurs when pivot divides array poorly.
15. In Prim’s algorithm, what is used to select the next edge?
(A) Stack
(B) Queue
(C) Priority Queue
(D) Hash Map
Answer: (C)
Explanation: Priority queue helps pick minimum weight edge efficiently.
16. What is the recurrence relation for Merge Sort?
(A) T(n) = T(n−1) + O(1)
(B) T(n) = 2T(n/2) + O(n)
(C) T(n) = T(n/2) + O(n)
(D) T(n) = T(n−1) + O(n)
Answer: (B)
Explanation: Merge Sort splits into two and merges → T(n) = 2T(n/2) + O(n)
17. What is the time complexity to insert an element into a hash table (average case)?
(A) O(1)
(B) O(log n)
(C) O(n)
(D) O(n log n)
Answer: (A)
Explanation: Hash tables offer average constant time for insert.
18. Which of the following is used to find Minimum Spanning Tree?
(A) Dijkstra’s
(B) Bellman-Ford
(C) Kruskal’s
(D) Floyd-Warshall
Answer: (C)
Explanation: Kruskal’s algorithm finds MST using greedy method.
19. (MSQ) Which algorithms are based on Divide-and-Conquer?
(A) Merge Sort
(B) Quick Sort
(C) Dijkstra’s Algorithm
(D) Binary Search
Answers: (A), (B), (D)
Explanation: Merge Sort, Quick Sort, and Binary Search divide the problem into subproblems.
20. (MSQ) Which of the following are true about Dijkstra’s algorithm?
(A) Works for graphs with negative weights
(B) Finds shortest path from a single source
(C) Can use a priority queue
(D) Gives correct results only for non-negative weights
Answers: (B), (C), (D)
Explanation: Dijkstra fails with negative weights. Works from a source using priority queue.
1. Which of the following is not accepted by a finite automaton?
Answer: (B)
Explanation: 0ⁿ1ⁿ is not regular; requires memory → needs a pushdown automaton.
2. Which among the following does a Pushdown Automaton (PDA) use for memory?
Answer: (B)
Explanation: PDA uses a stack to track context-free grammar productions.
3. Which language is not context-free?
Answer: (B)
Explanation: Language with equal number of a’s, b’s, and c’s (in order) is not context-free.
4. Which of the following is a correct statement?
Answer: (A)
Explanation: Regular ⊆ Context-free ⊆ Recursive.
5. What is the function of a transition in a Deterministic Finite Automaton (DFA)?
Answer: (C)
Explanation: DFA transitions from one state to another on an input symbol.
6. The pumping lemma is used to:
Answer: (C)
Explanation: Pumping Lemma is a contradiction tool to prove non-regularity.
7. A Turing Machine can be used to model:
Answer: (C)
Explanation: Turing machines can simulate any real-world computation.
8. Which of the following languages is undecidable?
Answer: (C)
Explanation: Halting problem is a classic undecidable problem.
9. In a DFA, what is the maximum number of transitions from a state over a single input symbol?
Answer: (B)
Explanation: DFA has exactly one transition per symbol from each state.
10. The language generated by the regular expression (a|b)*abb is:
Answer: (A)
Explanation: The expression ensures string ends with abb.
11. What is the result of applying the Kleene star (*) on a language L?
Answer: (C)
Explanation: Kleene star → L* = ∪ Lⁿ for n = 0 to ∞
12. The minimum number of states in a DFA to recognize the language of strings over {0,1} divisible by 3 (in binary) is:
Answer: (C)
Explanation: Modulo 3 → DFA has 3 states (0,1,2 mod).
13. Which of the following automata models has infinite memory?
Answer: (D)
Explanation: Turing machine uses an infinite tape as memory.
14. Which language class is closed under union, concatenation, and Kleene star?
Answer: (A)
Explanation: Regular languages are closed under all three operations.
15. Which machine is used to accept context-free languages?
Answer: (C)
Explanation: PDA accepts context-free languages.
16. Which grammar is suitable for programming languages with nested structures?
Answer: (B)
Explanation: CFGs support nesting via recursion.
17. The set of all recursively enumerable languages is:
Answer: (B)
Explanation: RE languages are recognizable but not always decidable.
18. Which of the following is not true for regular languages?
Answer: (C)
Explanation: PDA is for CFGs; regular languages don’t need a PDA.
19. Which of the following are regular languages?
Answers: (A), (C)
Explanation: (B) and (D) are not regular.
20. Turing Machines can:
Answers: (A), (C), (D)
Explanation: TMs can simulate DFA and PDA, but Halting Problem is undecidable.
1. Which of the following is performed during lexical analysis?
Answer: (B)
Explanation: Lexical analysis scans input and produces tokens.
2. Which data structure is used in recursive descent parsing?
Answer: (C)
Explanation: Recursive descent uses the system call stack.
3. The output of syntax analysis is:
Answer: (C)
Explanation: Syntax analysis produces a parse tree based on grammar.
4. Which of the following is an example of intermediate representation?
Answer: (B)
Explanation: TAC is used during intermediate code generation.
5. Which phase assigns memory to variables?
Answer: (D)
Explanation: Runtime environment handles memory layout and management.
6. Which of the following parsing techniques is top-down?
Answer: (C)
Explanation: LL(1) is a top-down parsing method.
7. In a typical compiler, which phase comes after syntax analysis?
Answer: (C)
Explanation: Semantic analysis checks for meaning after syntactic structure.
8. Which of the following statements is true for peephole optimization?
Answer: (C)
Explanation: Peephole optimization works on a small window of instructions.
9. What does the common subexpression elimination (CSE) do?
Answer: (B)
Explanation: CSE avoids recomputing the same expression multiple times.
10. Which of the following analyses is used to detect dead code?
Answer: (B)
Explanation: Liveness analysis finds variables whose values are never used.
11. Which of these is not a component of a grammar?
Answer: (C)
Explanation: Semantic actions are used during translation, not grammar.
12. Syntax-directed translation applies semantic rules to:
Answer: (B)
Explanation: Semantic rules are applied on parse tree nodes.
13. Which of the following optimizations require control flow graphs?
Answer: (D)
Explanation: All these require understanding control flow structure.
14. Which code is the closest to machine code?
Answer: (C)
Explanation: Target code is machine-dependent output.
15. Which optimization can reduce loop overhead?
Answer: (B)
Explanation: Loop unrolling reduces the number of iterations and overhead.
16. What is constant propagation?
Answer: (A)
Explanation: It replaces variables with constant values during optimization.
17. Which of the following is not a type of intermediate code?
Answer: (D)
Explanation: Assembly is low-level, not an intermediate representation.
18. Which phase handles register allocation?
Answer: (B)
Explanation: Register allocation is part of code generation.
19. Which of the following are examples of data flow analyses? (MSQ)
Answers: (A), (B), (D)
Explanation: These require flow of data across basic blocks.
20. Syntax-directed definitions can be used to: (MSQ)
Answers: (A), (B), (C)
Explanation: SDDs enable parse tree decoration and code generation, not lexical error detection.
1. Which of the following is used by a process to request a service from the operating system?
Answer: (B)
Explanation: System calls provide an interface between a running program and the OS.
2. Which of the following is not a valid state of a process?
Answer: (D)
Explanation: Typical process states are new, ready, running, waiting, terminated.
3. Which of the following system calls creates a new process?
Answer: (B)
Explanation: fork() is used to create a new process.
4. The critical section problem arises in a system with:
Answer: (B)
Explanation: Critical section problems arise due to concurrent access to shared data.
5. A binary semaphore can have:
Answer: (A)
Explanation: Binary semaphores are used for mutual exclusion.
6. Which condition is necessary for deadlock to occur?
Answer: (B)
Explanation: Circular wait is one of the Coffman’s four necessary conditions for deadlock.
7. In Round Robin scheduling, the performance depends significantly on:
Answer: (C)
Explanation: The time quantum directly affects turnaround time and context switching overhead.
8. Which CPU scheduling algorithm may lead to starvation?
Answer: (B)
Explanation: SJF may indefinitely postpone long jobs if short jobs keep arriving.
9. Which of the following page replacement algorithms may suffer from Belady’s Anomaly?
Answer: (B)
Explanation: FIFO can show increased page faults with more frames (Belady's Anomaly).
10. Which data structure is used in virtual memory for page table mapping?
Answer: (D)
Explanation: Page tables are generally implemented using arrays for fast indexing.
11. In which memory allocation technique may external fragmentation occur?
Answer: (C)
Explanation: Contiguous memory allocation may leave unused holes in memory.
12. What is the main advantage of demand paging?
Answer: (C)
Explanation: Demand paging loads pages only when needed, reducing memory usage.
13. Which file allocation method allows direct access?
Answer: (D)
Explanation: Indexed allocation stores all block addresses in an index block, enabling direct access.
14. The working set model is used for:
Answer: (C)
Explanation: The working set model determines the pages needed by a process to avoid thrashing.
15. Which of the following statements is true about threads?
Answer: (C)
Explanation: Threads of a process share code, data, and open files.
16. Which of the following algorithms is not used for I/O scheduling?
Answer: (D)
Explanation: LRU is used for page replacement, not disk I/O.
17. The banker's algorithm is used for:
Answer: (C)
Explanation: Banker's algorithm ensures a system will not enter an unsafe state.
18. Which of these is a non-preemptive scheduling algorithm?
Answer: (A)
Explanation: FCFS is strictly non-preemptive.
19. Which of the following can lead to deadlock? (MSQ)
Answers: (A), (B), (D)
Explanation: Deadlock requires all of these except preemption.
20. Which of the following are types of inter-process communication (IPC)? (MSQ)
Answers: (A), (B), (C)
Explanation: File systems are not directly used for IPC, but shared memory, message passing, and semaphores are.
1. In an ER diagram, a weak entity is one that:
Answer: (C)
Explanation: Weak entities require a foreign key and a partial key to be uniquely identified.
2. Which of the following is not a basic operation of relational algebra?
Answer: (D)
Explanation: Nesting is not a basic operation in relational algebra.
3. The primary key of a relation:
Answer: (B)
Explanation: A primary key must have unique, non-NULL values.
4. Which normal form removes partial dependency?
Answer: (B)
Explanation: 2NF eliminates partial dependency (dependency on part of a composite key).
5. The JOIN operation in relational algebra is a combination of:
Answer: (B)
Explanation: JOIN is implemented by taking Cartesian product followed by selection.
6. Which of the following indexing structures allows for range queries efficiently?
Answer: (B)
Explanation: B-trees and B+ trees support range-based queries efficiently.
7. Which SQL command is used to remove a table?
Answer: (B)
Explanation: DROP TABLE permanently deletes a table and its structure.
8. Which operation is non-lossy?
Answer: (A)
Explanation: Natural joins ensure a non-lossy decomposition when proper conditions are met.
9. A foreign key:
Answer: (A)
Explanation: A foreign key references the primary key of another relation.
10. Which of the following schedules is conflict-serializable?
Answer: (A)
Explanation: Conflict-serializable schedules are those equivalent to some serial schedule.
11. What is the main advantage of B+ trees over B-trees?
Answer: (C)
Explanation: B+ trees store data only at leaf level, making range queries more efficient.
12. Which of the following is not a relational integrity constraint?
Answer: (D)
Explanation: Normal forms are not constraints; they are design principles.
13. A relation is in BCNF if:
Answer: (A)
Explanation: BCNF requires every functional dependency’s LHS to be a candidate key.
14. Which SQL keyword is used to remove duplicate records?
Answer: (B)
Explanation: SELECT DISTINCT is used to eliminate duplicate rows.
15. In 2-phase locking (2PL), which phase ensures no new locks are acquired?
Answer: (B)
Explanation: In the shrinking phase, no new locks are allowed; only releases happen.
16. What is the purpose of serializability in transactions?
Answer: (C)
Explanation: Serializability ensures consistency equivalent to serial execution.
17. Which of the following file organizations is best for equality search?
Answer: (B)
Explanation: Hashed files are efficient for equality-based lookups.
18. The purpose of the undo log is to:
Answer: (A)
Explanation: Undo logs are used to revert changes of uncommitted transactions.
19. Which of the following can cause anomaly in relational database design?
Answers: (A), (B), (C)
Explanation: Redundancy, partial and transitive dependencies lead to update, insert, delete anomalies.
20. Which of the following are ACID properties in transactions?
Answers: (A), (B), (C), (D)
Explanation: These are the four essential properties of transactions in database systems.
1. Which layer of the OSI model is responsible for end-to-end delivery of messages?
Answer: (C)
Explanation: Transport layer handles end-to-end communication, including reliability and flow control.
2. Which switching method requires the entire message to be received before forwarding?
Answer: (C)
Explanation: Message switching stores the entire message before forwarding, causing delay.
3. Which protocol is used to resolve an IP address to a MAC address?
Answer: (C)
Explanation: ARP (Address Resolution Protocol) maps IP addresses to MAC addresses.
4. The function of DHCP is to:
Answer: (C)
Explanation: DHCP (Dynamic Host Configuration Protocol) assigns IPs dynamically to devices.
5. In the data link layer, framing is used to:
Answer: (C)
Explanation: Framing helps in identifying start and end of frames in a data stream.
6. In distance vector routing, routers share:
Answer: (C)
Explanation: Distance vector routing uses periodic sharing of routing tables with neighbors.
7. CIDR notation /24 implies how many IP addresses?
Answer: (C)
Explanation: /24 implies 32 - 24 = 8 bits for host = 2⁸ = 256 IP addresses.
8. Which error detection technique uses a generator polynomial?
Answer: (C)
Explanation: Cyclic Redundancy Check (CRC) uses polynomials for error detection.
9. UDP is:
Answer: (B)
Explanation: UDP is a connectionless protocol and does not guarantee delivery.
10. TCP ensures congestion control using:
Answer: (D)
Explanation: TCP uses slow start, congestion avoidance, fast retransmit, and fast recovery.
11. Ethernet uses which medium access control method?
Answer: (A)
Explanation: Ethernet uses CSMA/CD for collision detection in a shared medium.
12. What is fragmentation in IP?
Answer: (B)
Explanation: Fragmentation is done when packet size exceeds MTU.
13. ICMP is used for:
Answer: (C)
Explanation: ICMP sends error messages like "destination unreachable", "time exceeded", etc.
14. What protocol is used for email transfer between mail servers?
Answer: (A)
Explanation: SMTP is used to transfer emails between servers.
15. Which routing algorithm uses a complete network topology?
Answer: (D)
Explanation: Link state routing algorithms maintain complete topology info.
16. NAT is used to:
Answer: (B)
Explanation: NAT maps private IP addresses to public IP addresses.
17. A socket consists of:
Answer: (B)
Explanation: Socket = IP address + Port number (to identify process-to-process communication).
18. Which protocol is used to retrieve domain names?
Answer: (C)
Explanation: DNS (Domain Name System) maps domain names to IP addresses.
19. Which of the following are Transport Layer responsibilities?
Answers: (A), (C), (D)
Explanation: Transport layer handles end-to-end delivery, flow control, congestion control (not routing).
20. In TCP, which mechanisms are used for congestion control?
Answer: (D)
Explanation: TCP uses slow start, fast retransmit, and window scaling to control congestion.
Get Started with Dedicated Practice: Log in to your student account at https://engineersinstitute.com to download the weekly Mock Test and Practice Sets. Practice diligently, as each test includes Detailed Solutions and Analysis Reports with shortcuts, tips, and tricks to master complex topics efficiently.
Historical Question Alignment EII’s resources have consistently reflected GATE exam trends. Here are key topics where questions matched recent years:
Tips to Practice Question Papers Effectively
Benefits of Scheduled Mock Practices
Have doubts or technical issues? Contact us at 9990357855 via WhatsApp for instant support!